Data Centres
No one single component is hosted in our offices.
The Data Centres physical security features a layered security model, including safeguards like custom-designed electronic access cards, alarms, vehicle access barriers, perimeter fencing, metal detectors, and biometrics.
Access to the data centre floor is only possible via a security corridor which implements multi-factor access control using security badges.
Only approved employees with specific roles may enter.
Data centres feature redundant power systems and environmental controls to ensure uninterrupted services.
Fire detection and suppression equipment helps prevent damage to hardware. Heat, fire, and smoke detectors trigger audible and visible alarms in the affected zone, at security operations consoles, and at remote monitoring desks.
Hardware
The software stack is exclusively based on Linux OS.
This homogeneous environment is maintained by proprietary software that continually monitors systems for binary modifications.
Servers runs automated mechanisms that are designed to enable SmartJog to monitor and remediate destabilizing events, receive notifications about incidents, and slow down potential compromise on the network.
Zero Trust Policy
One of our main defences against known, or unknown, malicious applications is to simply prevent any external application from executing on our devices and appliances.
Allowing the installation and the use of a broad range of applications could be seen by some as an advantage or an internal policy.
We do simply think it differently !
Such a policy represents a massive risk to our devices and your media data from these applications.
The SmartJog hardware and software architecture is based on the zero-trust design, standing for the two principles :
- Deny All
- Allow None
Authentication process
The certificate contains a randomly generated unique identifier, with an identifiable per-service pattern.
Near the expiration period, the user is alerted informing of the end of validity.
If the certificate is valid, a new one can be requested by the same user.
A new certificate automatically invalidates any previous one, whether they were still valid or not.
Once the expiration date is over, any request made by the old certificate is rejected.
Access Control
We do provide a fine-grained access control of our business logic based on an implementation of Access Control Lists.
On top of the visibility control, we also check ACL rights for every service call. For instance, when the send process is called, we make multiple checks based on ACL rights to see if a user has proper rights to do a basic send. Then, we double-check the user ACLs to make sure the user has rights on an asset and rights on the destination.
We regroup our Access Controls on specific levels:
- On a per functionality level.
- On a Company level: a given user is associated to a Company and will inherit the Company’s default ACLs.
- Every User will have specific ACLs entrusted to them that will override the Company’s defaults.
On top of that, a critical aspect of our business logic has an audit trail that enables us to reference the origin of a change in explicit details. It is impossible for an end-user to change content without leaving a trace of the change, time of change, credential used, and leading as far as the originating IP address.
Altogether, every action that can be made can only be associated with a specific user, and is tracked on multiple levels, which ensures that no identity theft can be made if the end-user certificate itself was not compromised.
Data access and restrictions
Per contractual obligations, we offer our customers a detailed data processing amendment that describes our commitment to protecting customer data.
Customers data removal is immediate and irreversible. We do not keep it in any cache area.
We provide tools that make it easy for customers to take their data with them if they choose to stop using our services.
Support services are only provided to authorized customer administrators whose identities have been verified in several ways.
Data segregation
SmartJog logically isolates each customer’s data from that of other customers and users, even when it’s stored on the same compute server.
The SmartJog employees access rights and levels to access company resources are based on their job function and role.
Approvals are managed by workflow tools that maintain audit records of all changes.
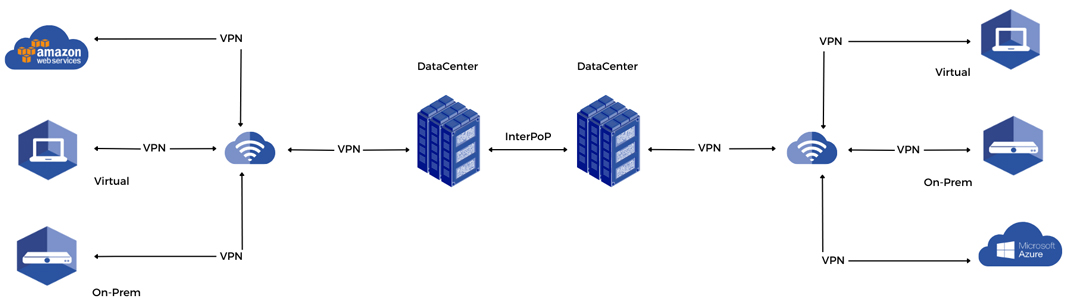
Data transfer engine
SmartJog uses a combination of two complementary technologies layers for transferring sensitive data.
The first one is in the form of a VPN.
In order to ensure the customers data remains safe when transferred through the public Internet, this “tunneling” process offers a secured transport channel through encryption and authentication methods.
All along the transfert, the data is transported through a VPN based on the WireGuard technology, a faster, simpler, leaner, and more performant technology than IPsec and OpenVPN.
The second technology relies on our accelerated network transfer protocols named RBC (Reliable Bit Cast). RBC was developed by SmartJog several years ago as an alternative to the proprietary software that was used to transfer files via satellite.
Equivalent to the other accelerated transfer protocols, RBC has been designed to work efficiently, even in the worst system and network conditions: high network latency, high packet loss, spontaneous IP address change, crash or reboot in the middle of a transfer, large files to be transferred, etc.
A file sent to a recipient is encrypted with a “unique per recipient” key. The file is only decryptable by the specified recipient.
Interrested by the SmartJog plateform and services ?
Contact our sales team or request for a demo
